Endpoint detection and response for advanced and emerging threats
Prevent, detect, and contain attacks in real time through a single, low-overhead agent across Mac and Windows.
All systems, all devices, one endpoint solution
Protection that’s always on and always improving
Real-time behavioral analysis, Iru AI, and our leading in-house research team ensure that unknown threats are stopped before lateral movement occurs.

Security built for the AI era
Iru AI evolves continuously, modeling millions of detections and endpoint events to spot patterns of malicious or anomalous behavior.

Dedicated in-house research
Our security research team tracks emerging techniques and new attack vectors, turning endpoint insights into proprietary models that catch what threat feeds miss.

Fast to deploy, easy to manage
Reduce security & IT overhead with one lightweight agent, unified with Endpoint Management. A focused UI helps lean teams investigate quickly and respond with confidence.
Top performer in independent tests
Ranked for top macOS malware detection and lightweight footprint.
- More zero-day exploits stopped
- 2.3x
- Lower resource usage under peak loads
- 22%
Stay informed about every response
Every action that’s taken is cataloged and analyzed, turning each detection event into a learning experience, both for your team and for the Iru AI context model.

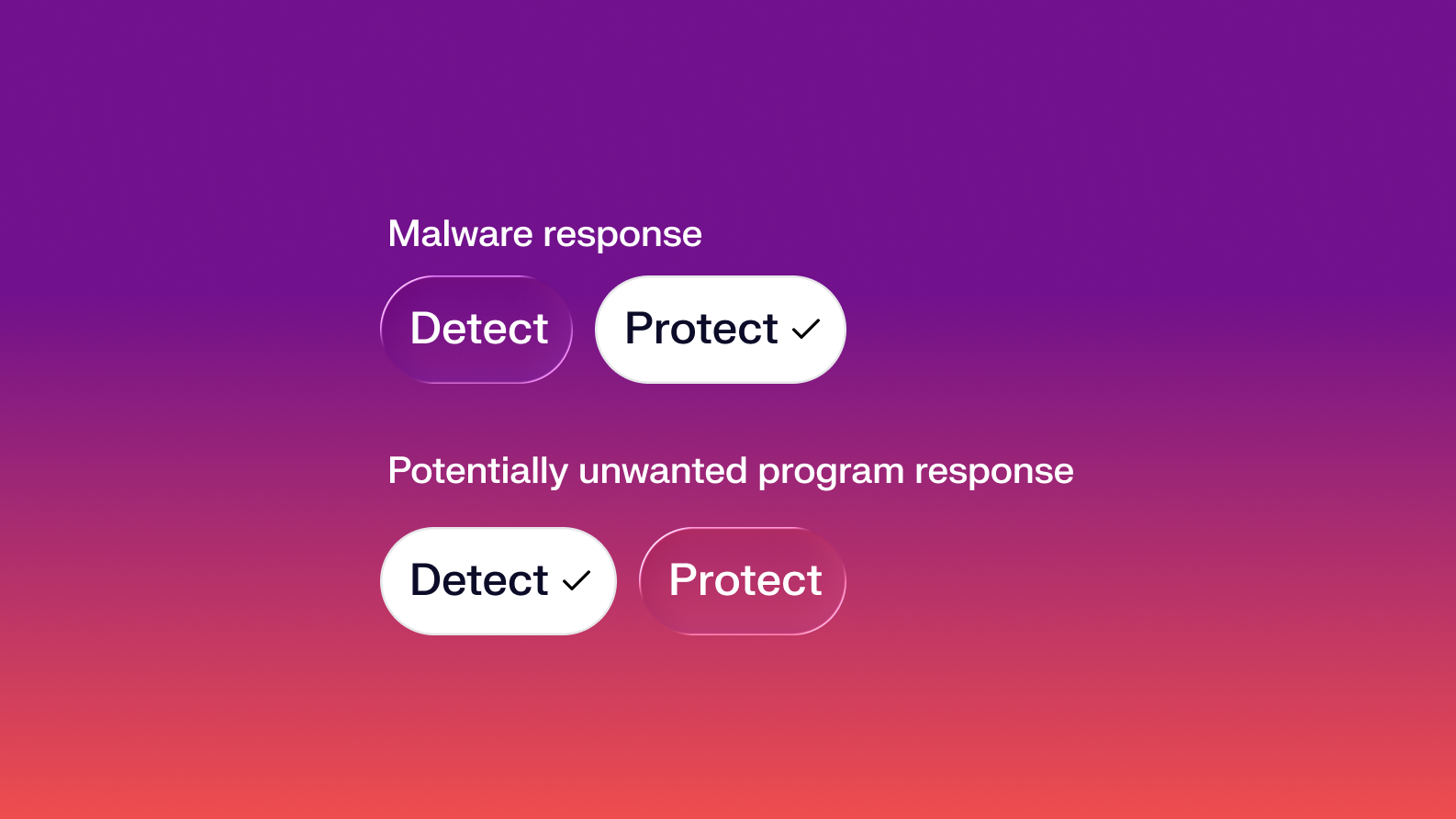
Flexible response to different threats
Protect Mode terminates malicious processes and quarantines files. Detect Mode gives observability without enforcement, ideal for pilots or sensitive cohorts.
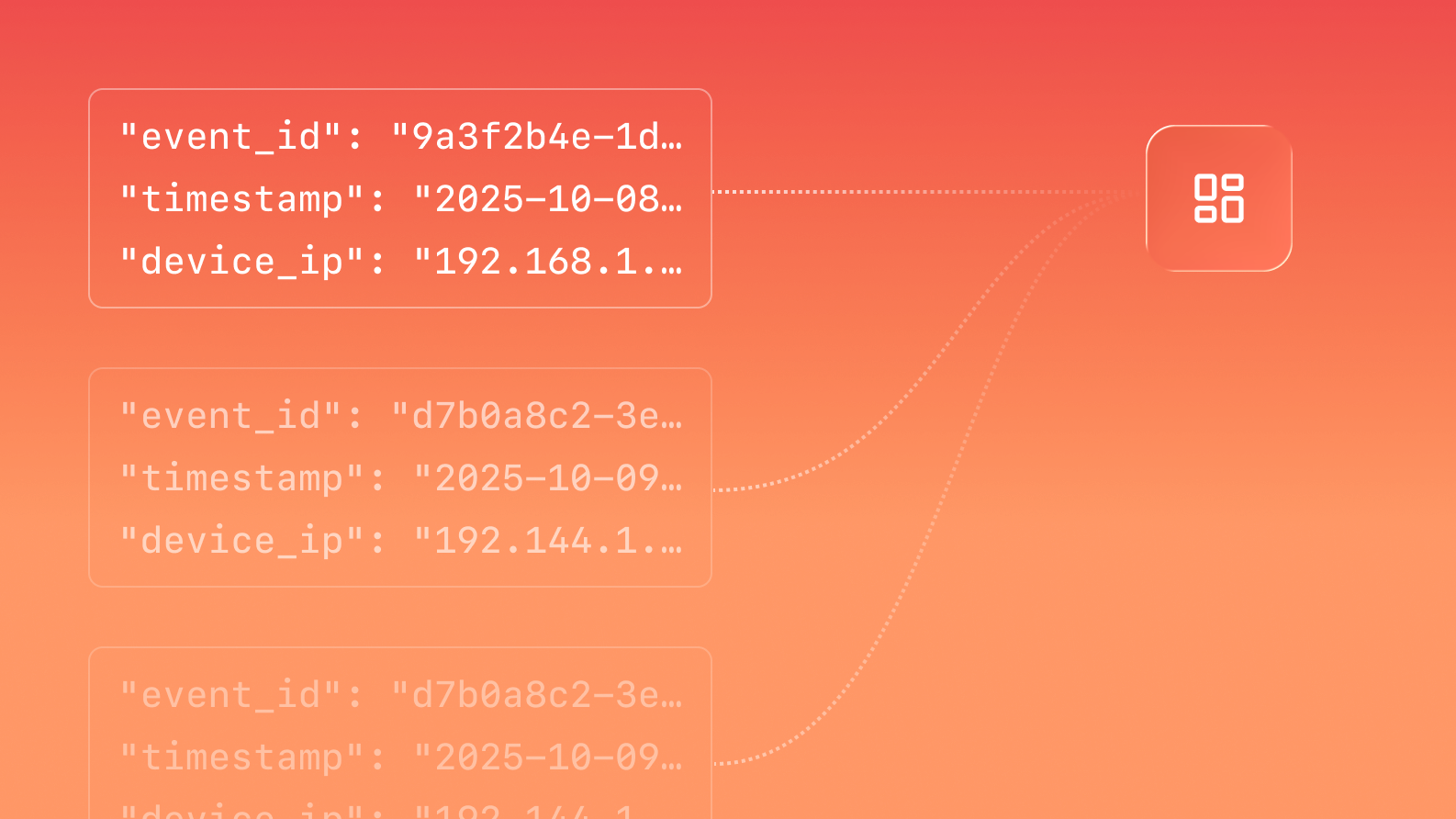
Pipe data to where you need it
Stream EDR events and tenant activity logs to your Amazon S3 bucket for SIEM ingestion, deeper analysis, and workflow triggers.
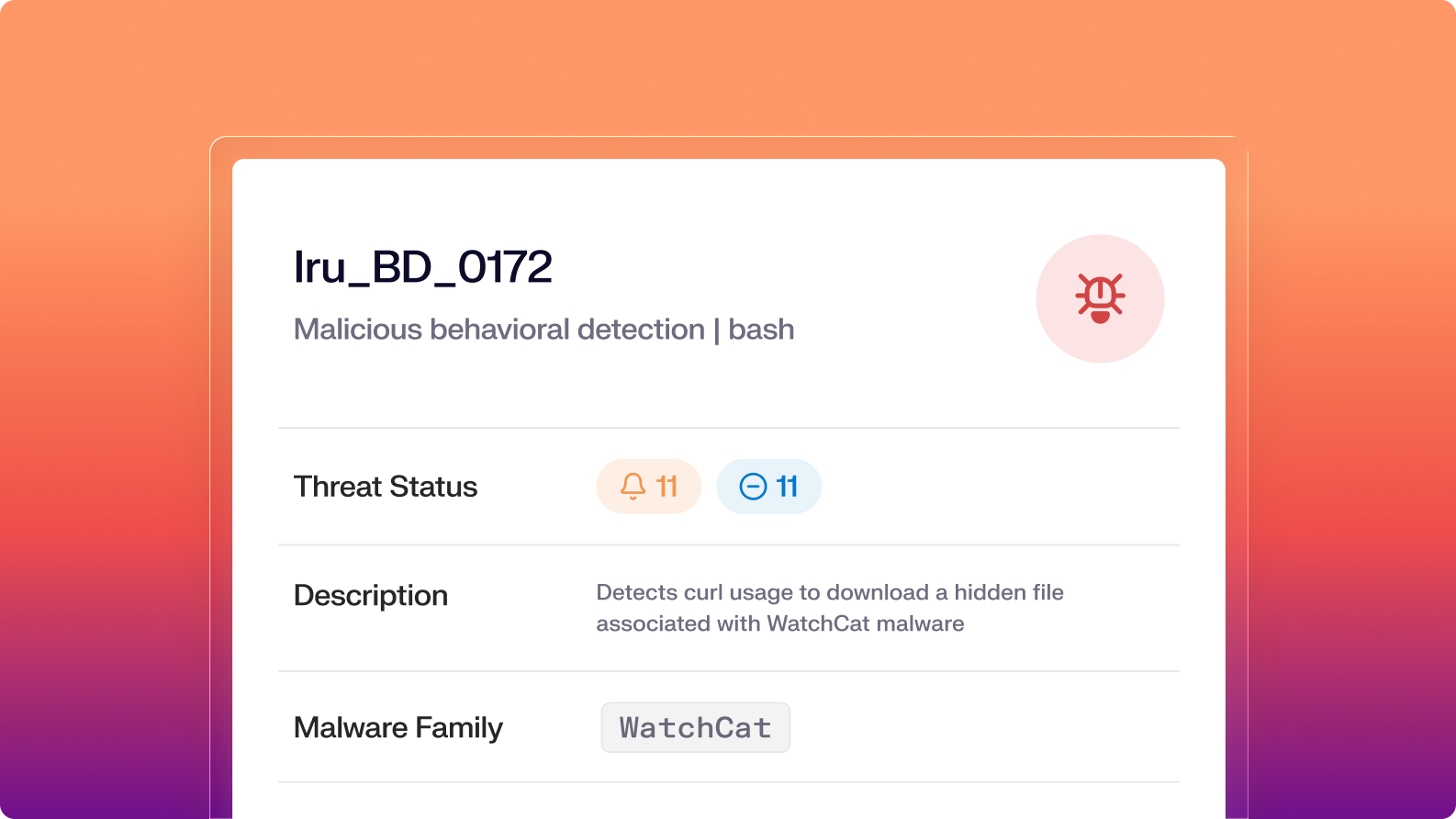
Threat-centric view
Investigate each event with a clear timeline of processes, files, behaviors, and affected hosts and users, so you can easily assess impact.
Endpoint Detection & Response features

File detections
AI-enhanced file analysis stops malware and unwanted programs. Backed by Iru's Security Research team and global threat feeds.
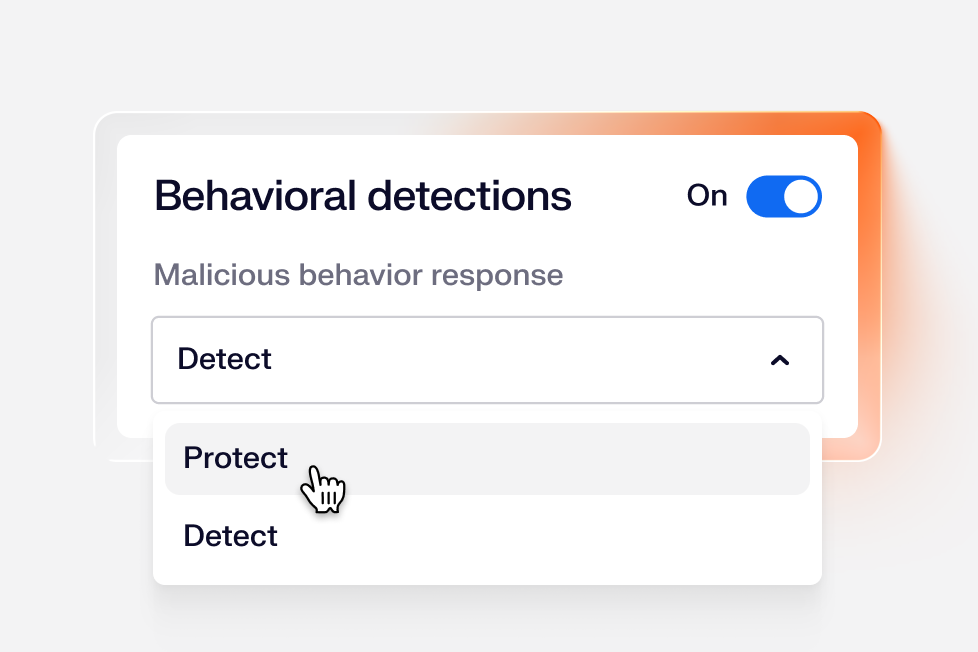
Behavioral detections
Real-time process monitoring tracks process chains and command-line activity to catch novel attacks early and stop lateral movement fast.
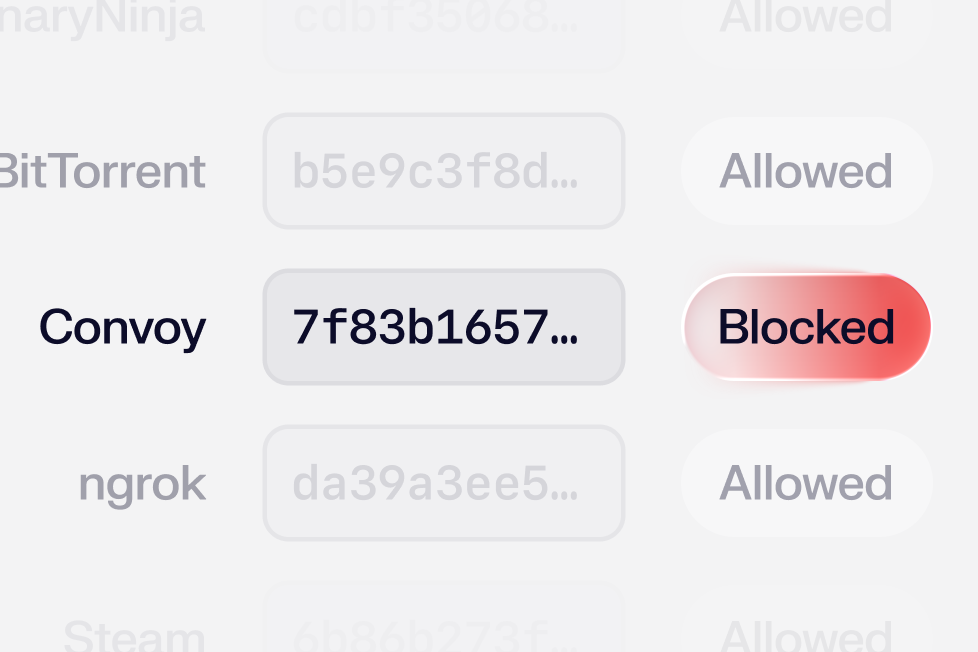
Allow and block
Allow or block files by hash, path, or publisher. Allowed items are ignored; blocked items trigger a detection and quarantine.
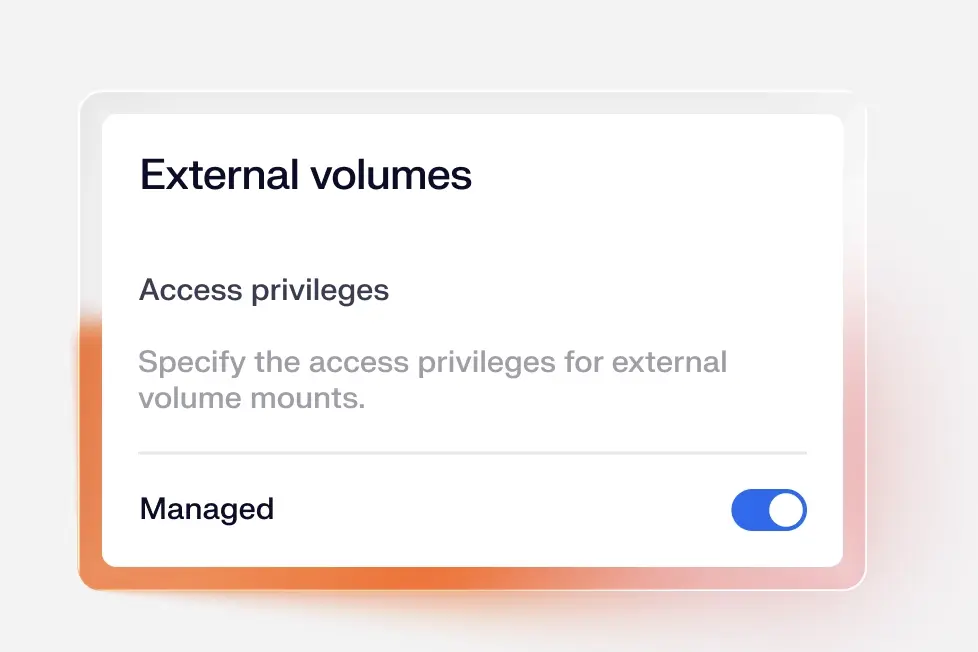
Storage controls
Lock down removable media and network volumes with encryption and access permission controls for USB drives, DMGs, SD cards, and server shares.
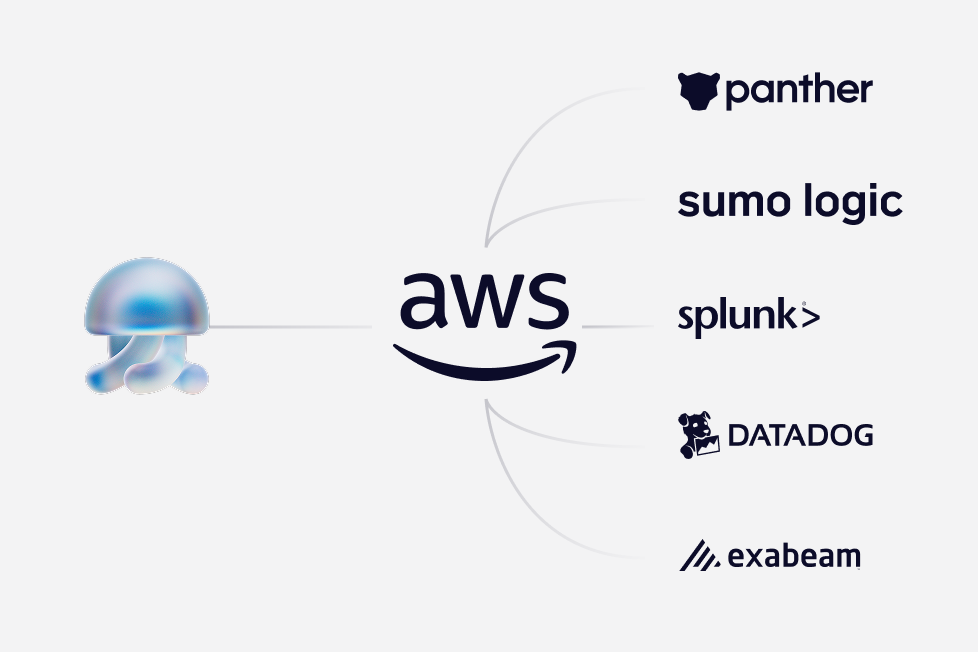
Amazon S3 Integration
Stream EDR events and tenant activity logs to your Amazon S3 bucket for SIEM ingestion, deeper analysis, and workflow triggers.
.png?width=400&height=400&name=Quote%20Logo%20(1).png)
Iru Platform
All the essentials in a single stack
A unified platform for your users, apps, and devices, woven together by Iru AI, giving time and control back to IT & security teams.
Learn more about Endpoint Management
Secure and control devices with unified endpoint management.
Learn more about Vulnerability Management
Unify vulnerability detection, prioritization, and autonomous remediation.
Learn more about Workforce Identity
Eliminate passwords entirely and provide effortless single sign-on to apps.
Learn more about Compliance Automation
Stay audit-ready with AI-generated controls and adaptive evidence mapping.
Learn more about Trust Center
Accelerate deals with a public portal for your security and compliance posture.
Learn more about Iru AI
Turn context into insights and actions with agentic AI across the entire Iru suite.
Let your team focus on what matters
Iru replaces fragmented tools with one AI-powered platform, so IT & security spend less time chasing tickets and more time improving the business.
